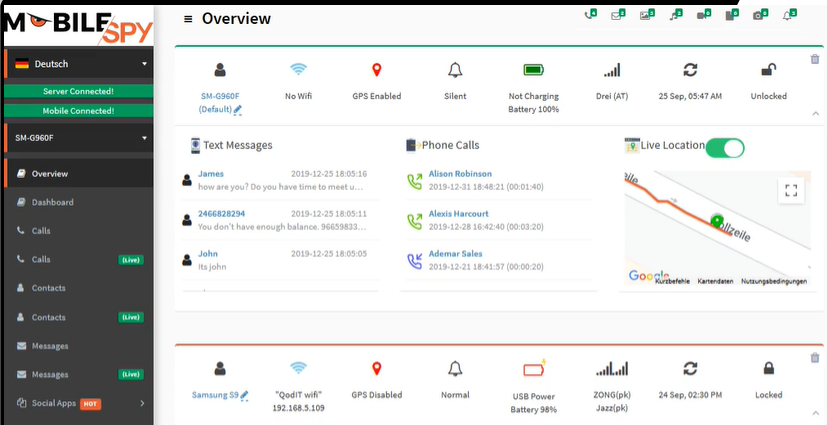
Pegasus spyware has become a symbol of intrusive government surveillance. Developed by the NSO Group, it grants attackers near-total access to a targeted device, raising serious privacy concerns. This article explores Pegasus, how to identify a potential infection, and what steps you can take to protect yourself.
What is Pegasus Spyware?
Pegasus is classified as zero-click spyware, meaning it can infect a device without any user interaction. Often delivered through links or malicious attachments, Pegasus can exploit vulnerabilities in popular operating systems like iOS and Android. Once installed, it becomes incredibly difficult to detect, operating silently in the background.
Pegasus Capabilities:
Pegasus is a powerful tool, granting attackers a vast array of capabilities, including:
- Data Extraction: Access to call logs, text messages, emails, photos, and other user data.
- Live Monitoring: Real-time interception of calls, messages, and even activation of the microphone or camera for live surveillance.
- Location Tracking: Monitoring the device’s GPS location.
How to Spot a Pegasus Infection (Indicators of Compromise):
Due to its sophisticated nature, detecting Pegasus can be challenging. However, some red flags might indicate an infection:
- Unexplained Battery Drain: Spyware can drain your battery life significantly due to constantly running processes.
- Unusual App Activity: Unfamiliar apps you didn’t install or unexpected background activity could be signs of intrusion.
- Overheating: The device overheating without intensive use might signify hidden processes.
- Decreased Performance: A noticeable slowdown in performance can be a potential indicator.
Important to Note: These signs are not foolproof and can occur due to other reasons. If you suspect an infection, it’s crucial to seek help from cybersecurity professionals.
Protecting Yourself from Pegasus:
While there’s no guaranteed way to prevent Pegasus infection, you can significantly reduce the risk:
- Keep Software Updated: Software updates often patch vulnerabilities exploited by Pegasus.
- Beware of Unidentified Links and Attachments: Don’t click on suspicious links or open attachments from unknown senders.
- Use Strong Passwords and Multi-Factor Authentication (MFA): Complex passwords and MFA add an extra layer of security.
- Install Security Software: Consider installing reputable mobile security software that can offer real-time protection.
What to Do If You Think You’re Infected:
If you suspect Pegasus infection, here’s what to do:
- Backup Your Data: Securely back up your data on a trusted external drive before attempting any fixes.
- Seek Professional Help: Consult a cybersecurity professional to diagnose the infection and recommend the best course of action. In some cases, a complete device wipe might be necessary.
You can Hire a Hacker online to scan, protect, and keep your device safe. As this spyware cannot be detected easily, only a professional ethical hacker can go deeper and identify whether you are affected or not.
- Report the Incident: Consider reporting the incident to the relevant authorities or organizations to help track the spread of Pegasus.
Pegasus: A Cause for Concern
Pegasus spyware signifies a worrying trend in government surveillance. While it might be difficult to definitively identify an infection, vigilance, and good security practices are crucial to protecting your privacy. Stay informed about the latest threats and prioritize software updates. If you suspect an infection, don’t hesitate to seek professional help. By working together, we can make it harder for intrusive spyware like Pegasus to operate in the shadows.